The #1 Employee App for Your Frontline Teams
Connect your frontline workers with everything they need to do great work.
Or schedule a demo with one of our product experts
With 1 million+ connected frontline workers worldwide






What’s Beekeeper?
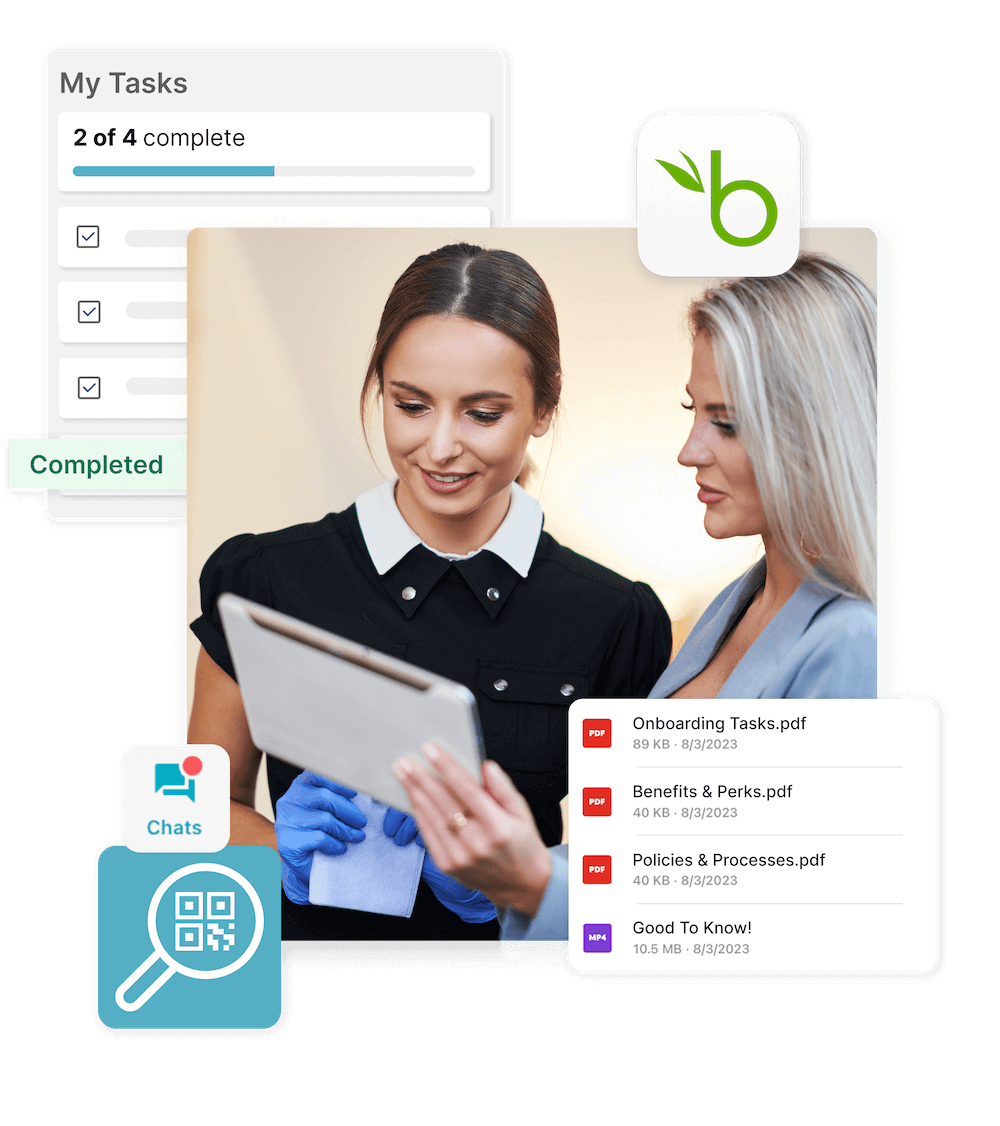
Use Beekeeper to connect your deskless workers to the people, systems, tools, and information they need to succeed. From paystubs to shifts, daily tasks and checklists, and multilingual communication: teams access everything in one place, designed for how they work.

Deliver a Superior Employee Experience
Frontline employees work differently than office staff. Bulletin boards, intranets, and personal apps don’t cut it. Provide easy mobile access to important info like shifts, paystubs, training, and recognition – securely, all in their pocket.
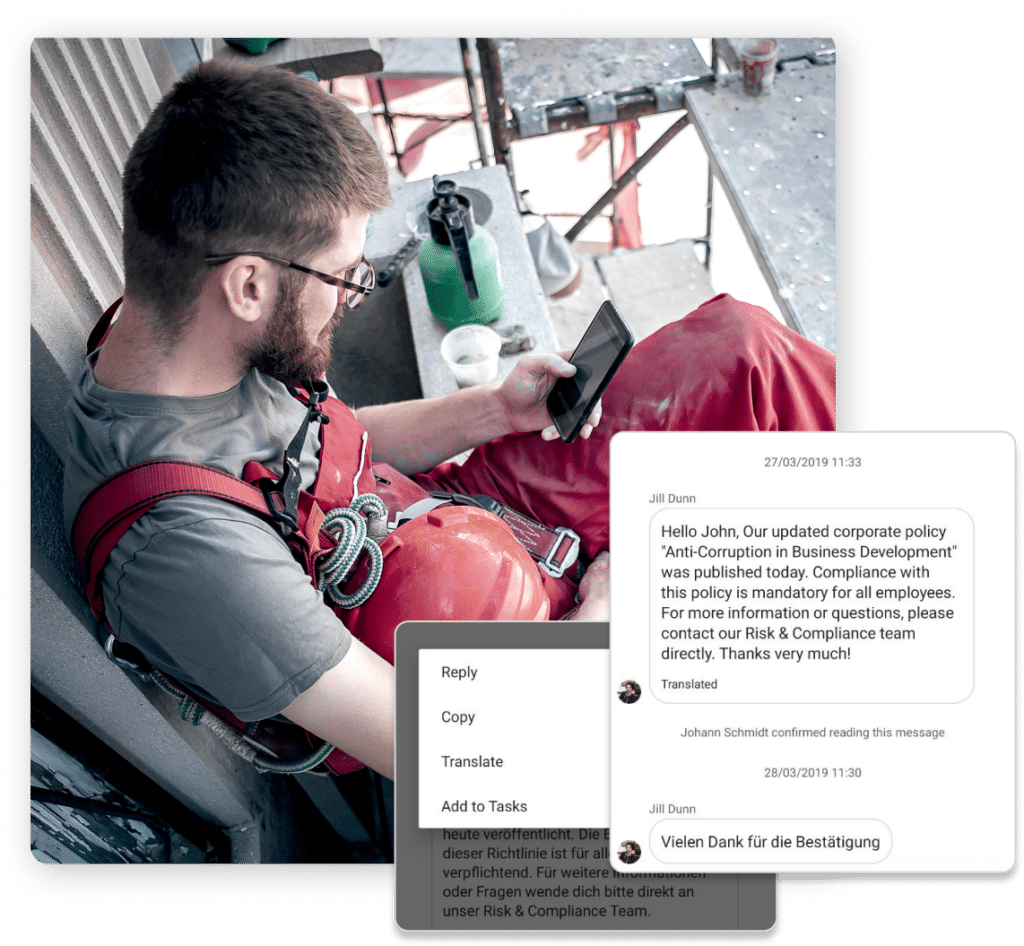
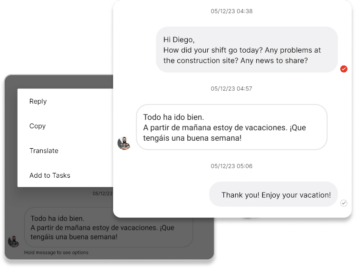
Instant & Easy Communication
From corporate comms to daily shift notes, translate information into 100+ languages in real-time. Effective communication fuels stronger collaboration and increases engagement.

Simplify & Automate
Streamline checklists and daily tasks by replacing paper forms. Assign and shuffle work in seconds, automate repetitive tasks, and check progress in real-time.


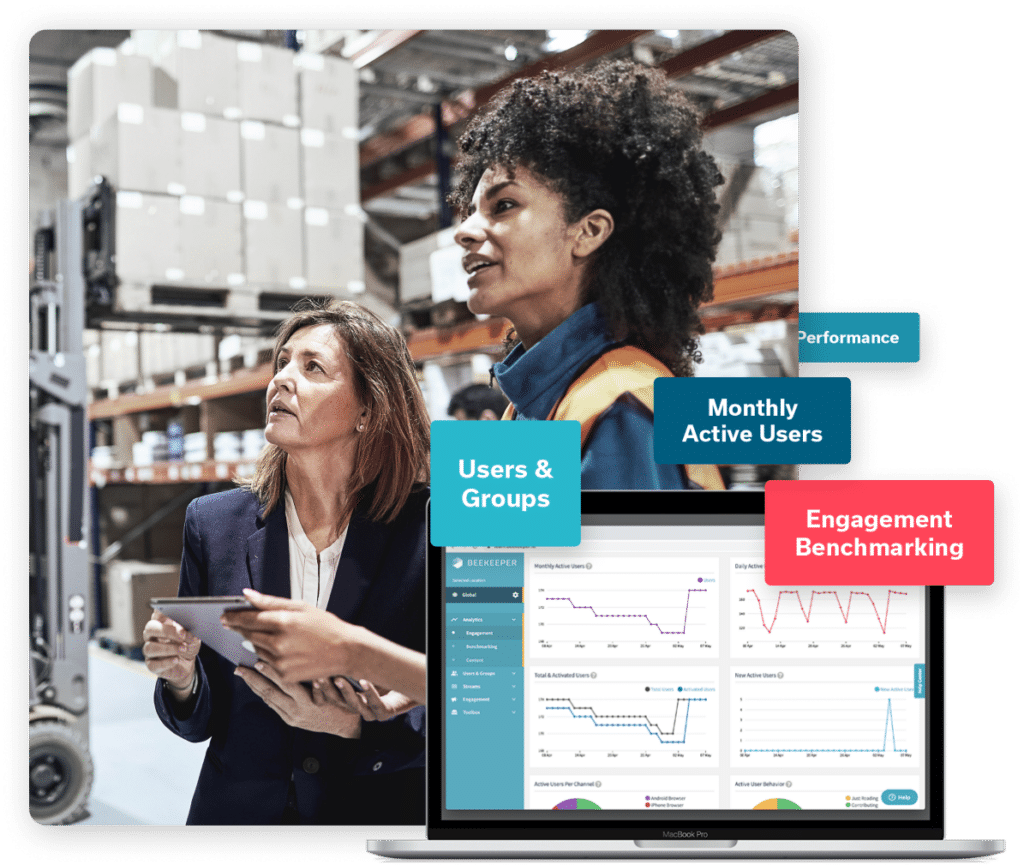
Stay Informed on Employee Engagement
Capture data that used to be hidden in paper forms and spreadsheets. Monitor everything on-the-go from your dashboard on the web, tablet, or mobile device. Managers make better decisions while offering the best possible employee experience.

Integrate All Your Tools
Save time and IT costs with easy, out-of-the-box integrations, dedicated configuration support, and automated workflows. You can even create custom integrations or workflows with Beekeeper’s open API and suite of tools for developers.

“In the old days, safety audits were paper-based, done manually. Today, we have optimized these processes with Beekeeper in a digital way – workers can enter the information on the spot, then group leaders get an immediate alert if something is unsafe and can then take action focusing on finding solutions to the unsafe situation.”

Heinrich Supthut
Manufacturing Manager

“To date, we have promoted 107 field leaders, all of whom are highly engaged on Beekeeper. 52% of those same field leaders are still at the company. With the cost to train, hire, and onboard field leaders, that positively impacted our business with $168,000 in savings on increased retention.”

Tamara Palmer
Internal Communications Manager

“Beekeeper has allowed us to digitize some of our operational processes like colleague shift management and daily briefings. There are also benefits we didn’t anticipate, such as the popularity of employees sharing personal stories and chiming in to recognize each other’s achievements.”

Mitch Austin
Communications Security Manager

“More than 12,000 non-wired Cargill employees have opted into using this tool and are now easily connected to information, resources, and communication they didn’t have before.”

Jay Knoll
Sr. Communications Specialist